See Your Scanners
"Waterfall" Sharded Port Scan Visualization
Scanners distribute their scans across multiple IP addresses, which makes it difficult to track them. LightScope helps to put the sharded peices together.⌨️ Keyboard: WASD move, QE up/down JIKL rotate view
What is LightScope?
LightScope is free, open source software that gathers data for graduate cybersecurity research at the University of Southern California ISI. Those who deploy it are rewarded with rich threat intelligence about who's targeting their systems and how. The threat intelligence LightScope provides to users is enhanced through research partnerships with ipinfo, greynoise, and abuseIPDB.
What does the software do?
Observes attacker interactions with closed ports on live hosts, forwards that traffic to USC honeypots, and reports attackers to AbuseIPDB and ISPs.
What do you get for running it?
Detailed information about who's targeting you, automatic reporting of the malicious actors to ISPs, and personalized IP blocklists.
What DOESN'T it do?
It's not antivirus or Endpoint Detection and Response (EDR), and it won't slow down your system like they do. It's also not a Web Application Firewall (WAF), and it doesn't examine traffic to running services such as webservers (for privacy reasons).
Why should I run it?
- See who's attacking your server
- Find out if your laptop is getting attacked on public Wifi
- Discover compromised routers/smart TVs scanning your home network
- Support open cybersecurity research
What data do you collect?
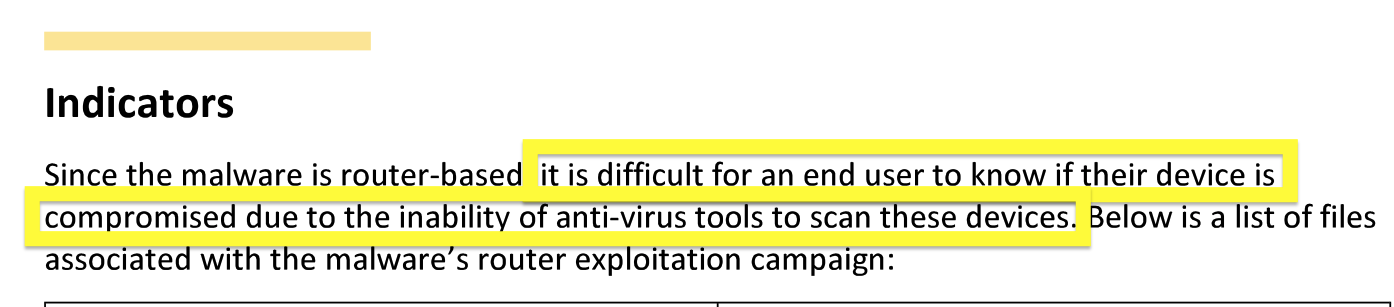
We are interested in the traffic scanners and attackers send to closed ports on your servers. Your IP is fully anonymized and we do not collect any identifiable data about your machine. We went through IRB to certify our methods. A full list of data collected can be found in FAQs.
Why are you doing this?
To help people who can't afford expensive services. To collect data in support of PhD research.
Is it actively supported?
Yes.
How do I contact you?
How do I install it?
What are your research questions?
LightScope Research Overview
LightScope is a free, open source cybersecurity research initiative that examines unwanted traffic from attackers and scanners. LightScope is different from existing solutions as it turns closed ports on live machines into network telescopes/honeypots, and transparently forwards attacker traffic to USC managed honeypots. This removes the risk of running honeypots on production systems, and makes LightScope difficult for attackers to detect and avoid (unlike traditional honeypots and network telescopes). All this leads to better data for researchers and network operators.
Although it's broken out into two applications (laptop/home computers vs servers), they're really just two use cases for the same tool. The main difference is that unwanted/scan traffic is expected on public facing servers, but should never be seen on home networks or public wifi networks.
LightScope is only interested in unwanted traffic attackers/scanners are sending you. If you're running a webserver or some other application, LightScope will ignore traffic to and from it. We only look at what gets sent to your closed ports, where no legitmate services are running.
The LightScope client is free, open source, extremely lightweight, and designed to run on production machines. If you install it you will be provided with rich information about who's targeting your network and tailored IP blocklists you can use.
LightScope is provided by the University of Southern California Information Sciences Institute.
LightScope For Servers
LightScope turns closed ports on your server into network telescopes, and transparently forwards attacker traffic to USC managed honeypots. This removes the risk of running honeypots on production systems, and makes LightScope difficult for attackers to detect and avoid (unlike traditional honeypots and network telescopes). All this leads to better data for researchers and network operators.
LightScope is only interested in unwanted traffic attackers/scanners are sending you. If you're running a webserver or some other application, LightScope will ignore traffic to and from it. We only look at what gets sent to your closed ports, where no legitmate services are running.
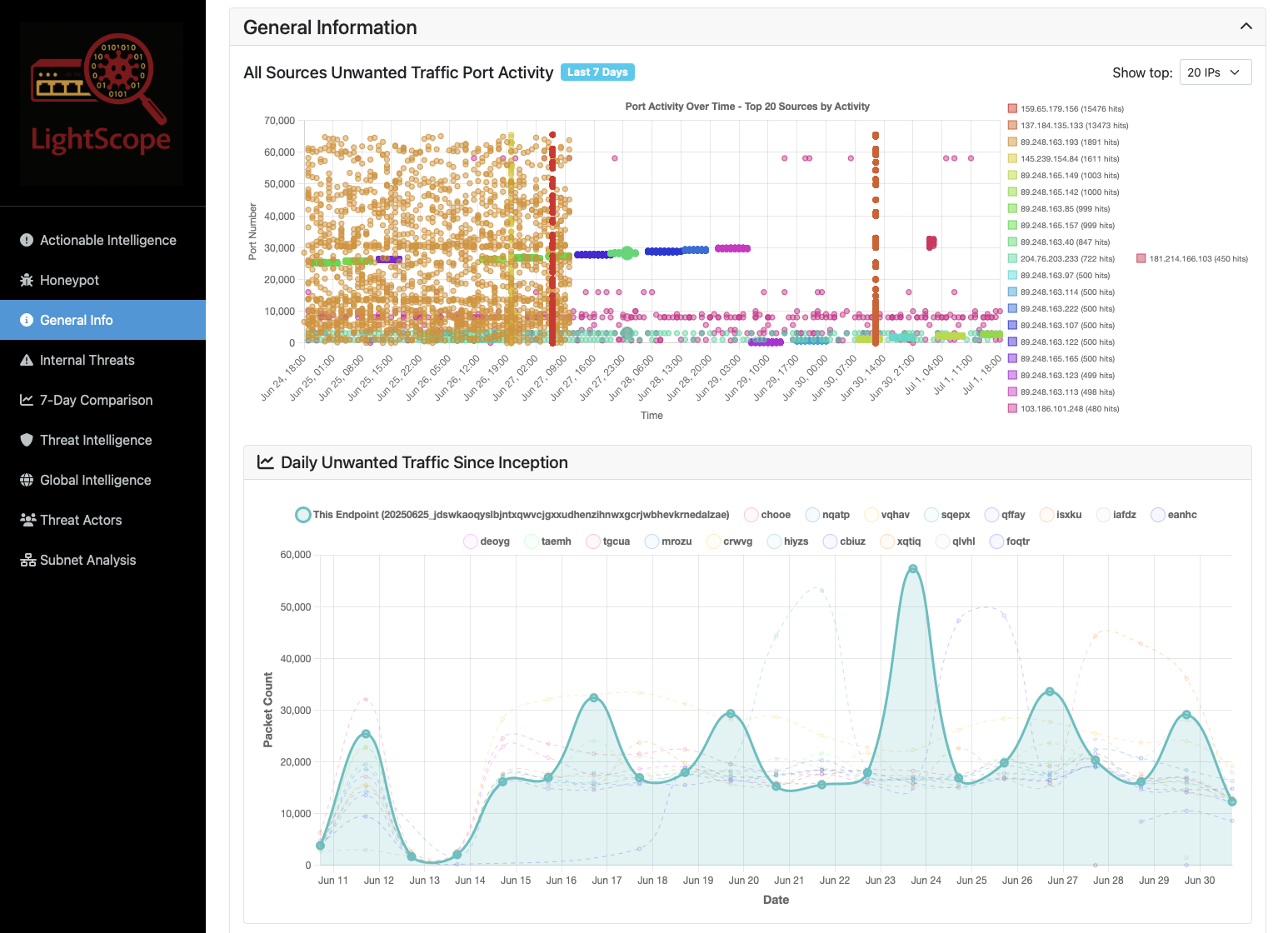
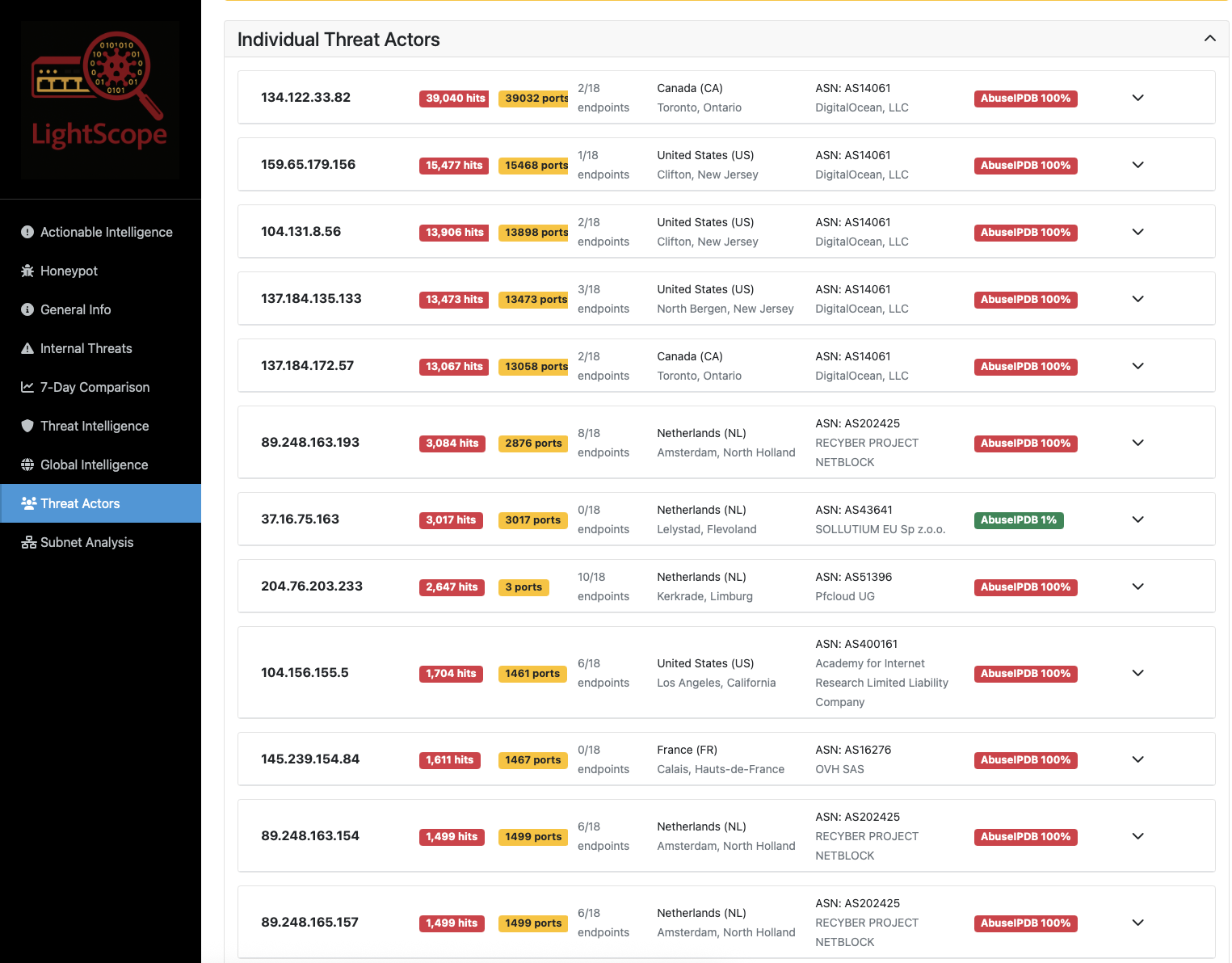
The LightScope client is free, open source, extremely lightweight, and designed to run on production machines. If you install it you will be provided with rich information about who's targeting your network and tailored IP blocklists you can use to keep your network safe. Please click on one of the images below and select a public enpoint to view the type of data you will recieve.
Who's Targeting You?
Support Cybersecurity Research at the University of Southern California, and the Open Source Community!
See who's targeting your systems • Get custom IP blocklists • Help us make the internet safer.